



 accesses since February 4, 2011
accesses since February 4, 2011
 copyright notice
copyright notice  link to the published version in Gaming and Leisure, Summer, 2011
link to the published version in Gaming and Leisure, Summer, 2011




 accesses since February 4, 2011
accesses since February 4, 2011
Stuxnet has proven that we live in interesting times.
For those of you new to Stuxnet, its 2011's biggest gift to cyberwarfare. At this writing, we're pretty confident that we understand what it does/did. As to who did it, not so much.
Stuxnet is basically an enhanced "worm" that begins life on a removable storage device. Stuxnet has an interesting, albeit complicated, genesis. According to the Symantec W32.Stuxnet Dossier (www.symantec.com/connect/blogs/w32stuxnet-dossier), "Stuxnet is one of the most complex threats we [Symantec] have analyzed.... Stuxnet is a large, complex piece of malware with many different components and functionalities." Although the Stuxnet package was discovered in late 2010, many of its components were derived from well-known malware dating back to 2005.
From an evolutionary point of view, Stuxnet's DNA derives from several sources, including:
Several of these vulnerabilities were exploited and the drivers registered with Verisign under a variety of legitimate corporation's certificates. The parent Stuxnet encrypted DLL files are embedded in a self-executable wrapper program that acts as the "dropper." On execution, the wrapper extracts the DLLs and support utilities, loads them into a computer's memory, and calls the export routines for further propagation. The business part of Stuxnet is a rootket that is optimized for a programmable logic controller (PLC) used in control systems. Although some parts of Stuxnet have been found wanting in terms of code quality, Stuxnet as a whole has proven remarkably effective and resiliant. Symantec's Stuxnet timeline appears in Figure 1.
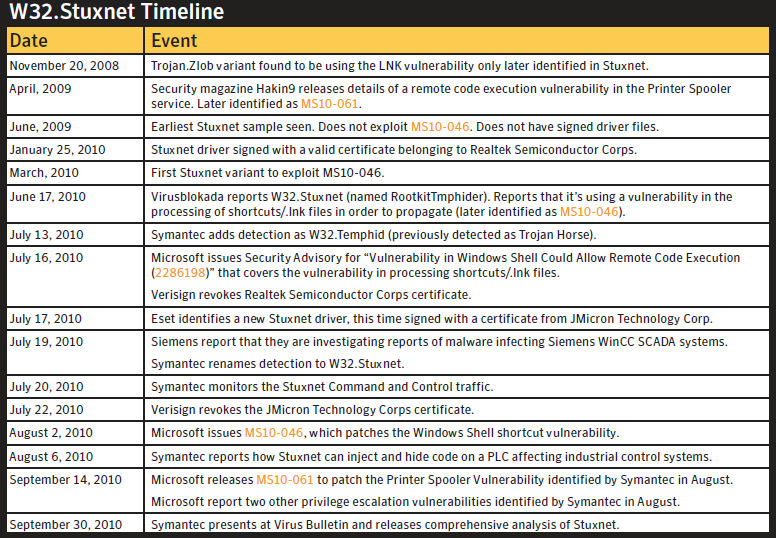
Stuxnet is focused on a particular type of control system develeped by Siemens called SCADA (supervisor control and data acquisition systems). It proved especially virulent on the P.C.S.-4 controller that is used to control uranium enrichment with centrifuges. You can probably see where this is headed.
Enter Dr. A.Q. Khan, the Pakistani scientist to whom Western media have attached the sobriquets "Merchant of Menace" for his suspected trafficking of weapons-level nuclear technology. Khan worked in the Netherlands in the 1970's in a laboratory (URENCO) that enriched Uranium for nuclear reactors. His status as senior scientist provided him with privileged access to enrichment technology and IP.
Natural uranium consists of three isotopes: U-238 (>99%), U-235 (.7%) and U-234 (the rest). U-235 is the stuff of which nuclear weapons are made. However, the uranium in a nuclear weapon has to be at least 90% U-235. Anything less won't fizz. The solution is to convert uranium yellow cake into a uranium hexafluoride gas and spin it in a centrifuge. A high speed (~1,500 revolutions per second) centrifuge is ideal for creating a high concentration of U-235. The uranium gas separates with the heavier U-238 driven to the bottom of the containers while U-235 remains at the top. The lighter U-235 is continuously bled off through repeated processing, eventually yielding the infamous "weapons-grade uranium." This process was refined by a fellow named Zippe in the 1950's and 1960's. Zippe centrifuges were deployed in the Dutch lab where Khan worked.
This much is widely agreed upon. After that, Khan's history is subject to debate depending on one's allegiances. According to Western sources, Khan mis-appropriated secret, proprietary IP and technology from the Dutch lab for use in the Pakistani nuclear weapon's program. Khan bacame the head of Pakistan's uranium gas-centrifuge development program which duplicated the Dutch Zippe centrifuge technology. The concentrate was satisfactory, and Pakistan ended up with their nuclear bomb.
Shortly thereafter, the Zippe centrifuge technology shows up in countries with which Khan and his associates had working relationships. In fact, Khan confessed in 2004 to exporting nuclear designs and technology of use in nuclear weapons development to North Korea, Libya, and Iran - although he has since recanted. In any case, all three countries ended up with the same PK-1 gas centrifuges that Khan developed in Pakistan. It turns out that PK-1 gas centrifuges use a version of the Siemen's SCADA controller discussed above. At this point, we've travelled full circle. Sure enough, the PK-1 controllers used the programmable logic controllers developed by Siemens for Step 7 software used to reprogram the PLCs.
According to media reports, the SCADA-controlled Zippe centrifuges remain in use in North Korea and Iran. Libya apparently decided that nuclear weaponry was dispensible and abandoned it's uranium enrichment program. It has been suggested that the Libyan equipment has found its way to labs within the Department of Energy and Unit 8200 on Mt. Avital in the Negev desert.
The most thorough analysis of Stuxnet that I've seen is Symantec's W32.Stuxnet Dossier (http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/w32_stuxnet_dossier.pdf). Though technical, this dossier makes interesting reading for those with a background in computer science or informatics.
We'll leave the technical issues to the reader. In broad terms, Stuxnet is a worm whose primary method of propagation is removable USB storage devices. It resembles a commercial-grade application in function. It has:
This is just a partial list of Stuxnet features. One of the interesting characteristics of Stuxnet is the fact that the HTTP packet payload used for command and control is this system information XORed with FF. I mention this because this is a pretty primitive encoding technique to obscure the payload. Some commentators cite this as evidence that at least the command and control programmers were not the sharpest knives in the drawer.
Stuxnet will run on virtually any recent Windows operating system - Win2k, XP, 2003 Server, Vista, 2008 Server, Windows 7.
What make Stuxnet interesting to the security community is its complexity and effectiveness.It is this complexity that suggests multiple teams of hackers and 10+ individuals were involved in its development. It's effeciveness suggests that the development was very focused on industrial controllers that use the Siemens Step7 PLCs -- like those used by Iran at its uranium enrichment centrifuge installation at Natanz. Figure 2 emphasizes this point.
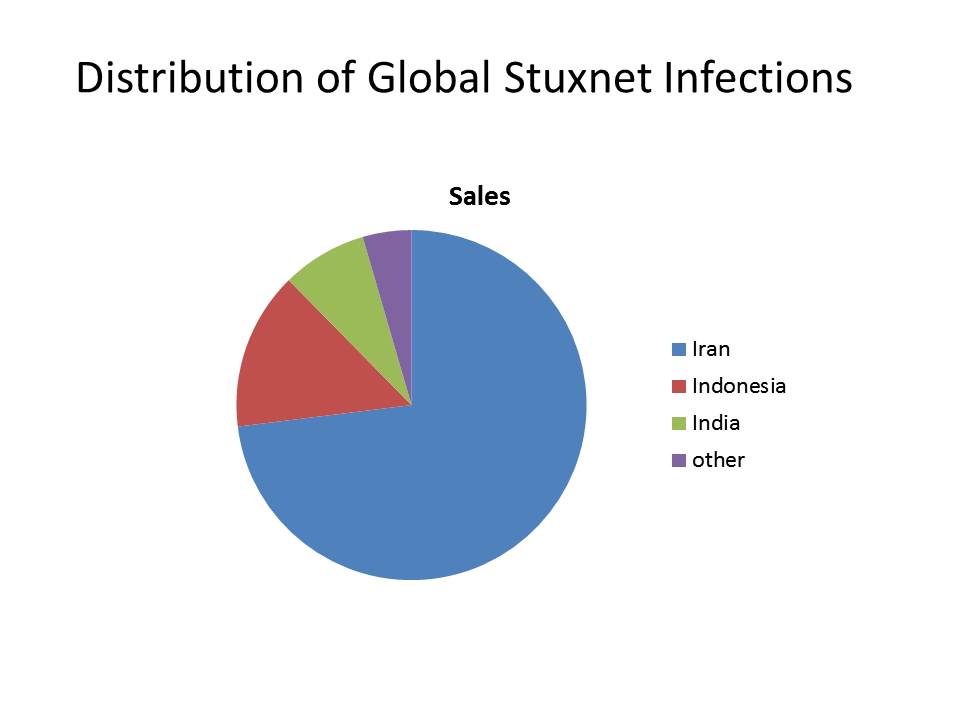
What was the effect of the Stuxnet attack? It depends upon who you listen to.
We may never know. However, Tom Parker of Securicon offers some refined speculation in his recent BlackHat D.C. presentation (1/18/11). To paraphrase Parker, if this is state-sponsored, it's probably a smaller state with limited resources because the code isn't as good as we would expect of a super-power. Whoever it was had access to Siemens' controllers to practice on. It was likely that the code was developed by at least five people comprising at least two teams of varying skill levels, the command and control team being the weakest.
All things considered, some level of U.S./Israel involvement should not be ruled out at this point. If no state-sponsored, perhaps state-aware?
In any case, Stuxnet definitely raises the bar for future CyberWarfare.